-

Embracing Distroless Containers for Secure Software Delivery
The evolution of containerization and the rise of cloud-native applications… Read More
-
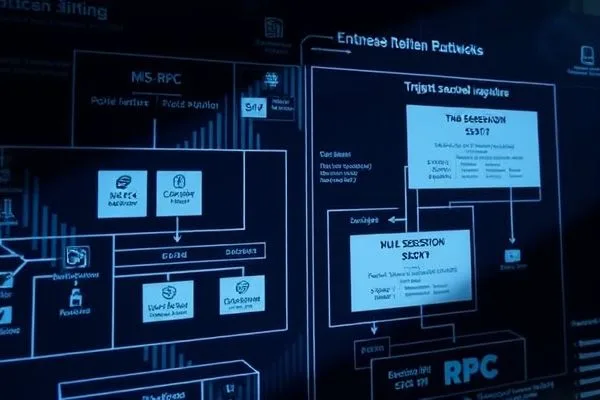
Exploring Null Session Vulnerabilities in Windows MS-RPC Interfaces
As cybersecurity threats evolve, the potential vulnerabilities associated with null… Read More
-

Ivanti Vulnerability Leads to Exploit of TRAILBLAZE and BRUSHFIRE Malware
In an age where cybersecurity threats lurk around every corner,… Read More
-
Emerging Cyber Threat: WRECKSTEEL Malware Targeting Ukrainian Infrastructure
The rapid advancement of technology brings with it a formidable… Read More
-

Critical Flaw in Apache Parquet Allows Remote Attackers to Execute Arbitrary Code
The discovery of a severe vulnerability in Apache Parquet’s Java… Read More
-

Microsoft Alerts on Tax-Season Phishing Using PDFs and QR Codes
In an era where phishing attempts are on the rise,… Read More
-

Lazarus Group Exploits Job Seekers with ClickFix Tactic and GolangGhost Malware
As cybersecurity threats evolve, understanding the tactics employed by malicious… Read More
-

AI Threats Are Evolving Fast Learn Practical Defense Tactics in this Expert Webinar
Artificial intelligence is transforming the landscape of cybersecurity, posing both… Read More
-

AI Adoption in the Enterprise: Overcoming Security and Compliance Challenges
AI adoption in enterprises presents both significant promise and formidable… Read More
-
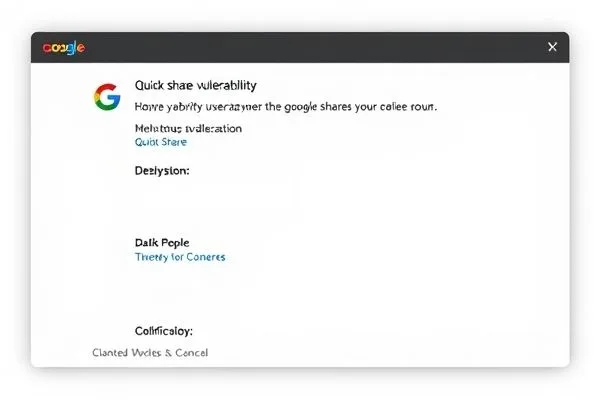
Google Resolves Silent File Transfer Vulnerability in Quick Share
Did you know that a recently disclosed vulnerability in Google’s… Read More
Search
-
Fortinet Alerts on SSL-VPN Symlink Exploit in FortiGate Devices
Consider the ramifications of a vulnerability that allows unauthorized access even after patches have been applied. Recent revelations from Fortinet…
Subscribe to our newsletter!








